The average individual is at the mercy of cyber criminals, who either dupe him of his money by gaining access to his banking passwords using his phone or hold him ransom by locking the device

Cyber crooks stealing money, data from cellphone
 In its continuing investigation into data theft and cyber security crimes in Indian banks, BPOs, and big businesses, mid-day has found that not only big organisations but also individuals and average computer users are being duped of their hard-earned money by cyber criminals, who make use of their mobile phones to gain access to crucial passwords.
In its continuing investigation into data theft and cyber security crimes in Indian banks, BPOs, and big businesses, mid-day has found that not only big organisations but also individuals and average computer users are being duped of their hard-earned money by cyber criminals, who make use of their mobile phones to gain access to crucial passwords.
ADVERTISEMENT
Also read: Mumbaikars beware! Your bank details are being stolen and sold!
Responsible for this is a nexus of banks and telecom firms, who are showing blatant disregard for the most basic security norms. In other cases, the fraudster takes over control of the device through malicious software and hands back control to the victim once he has paid a “ransom” amount.

Graphics/Vijay Pednekar
Banks are paying no heed to safety norms such as the Reserve Bank of India (RBI) guidelines and “Code of Bank’s Commitment” issued by the Banking Codes and Standard Board of India (BCSBI), appointed by the RBI.
They are also violating the key RBI rules declared in 2012, also known as the “Master Circular Know Your Customer (KYC) norms/Anti-Money Laundering (AML) standards/Combating of Financing of Terrorism (CFT)/Obligation of banks under PMLA, 2002”.
Some leading banks, even after having noticed a suspicious credit card transaction based on an unsatisfactory identification from the customer, have shied away from acting on it. Under such circumstances, it is obligatory for banks to file a Suspicious Transaction Report (STRs) to the Financial Intelligence Unit-India (FIU-IND), a government regulatory body.
Also Read: Facebook in soup over 'stealing' personal data
But many do not do so simply to ensure they do not have to share the liability or compensate victims adequately, recent government reports of state Information Technology department noted. The telecom firms are found guilty of violating the guidelines set by the Telecom Regulatory Authority of India, Department of Telecom (TRAI/DOT), on the issuance of SIM cards.
They have been found issuing cards without running a background check on the applicant, in the process issuing to fraudsters a duplicate copy, later used to carry credit card frauds from as far as Russia. “The individual customers/citizens do not have the wherewithal to fight the cyber criminals operating in total anonymity and across national boundaries, more proactive and consumer-friendly policies are needed on behalf of the banks, to safeguards the interests of their customers.
mid-day investigation: Here's how Mumbai's private hospitals are getting rich on 'blood money'
But many aren’t doing so,” reads an internal report prepared by the state adjudicating officer Rajesh Aggarwal, appointed to hear cases under Section 46 of the Information Technology Act (IT), 2000. Section 46 pertains to the provision of seeking civil remedy to recover financial losses incurred due to cyber fraud. The gross negligence of banks and telecom firms has resulted in a spate of card frauds in 2014, in which mobile and net-banking services were used to make payments from accounts of innocent customers and card holders.
Some of the most reputed banks and telecom firms the State Bank of India (SBI), Standard Chartered Bank, Bank of India (BOI), Bharti Airtel and Vodafone have been found guilty by the state government of leaking sensitive customer data, resulting in banking card frauds and losses to innocent citizens. They have also been officially slapped with fines ranging between Rs 1 lakh and Rs 10 lakh by the Maharashtra government, for violation of guidelines.
Add to this, the average computer user in India is now faced with a mass spamming attack that aims to encrypt data stored in the system and demand ransom to unlock it. If this is not enough, Mumbai is witnessing a spike in crimes related to spamming of Android phones with notorious malware and spyware capable of collecting information related to application programming interface (API) keys, GPS location, international mobile equipment identity (IMEI) numbers, network operator and other vital details of a device. These growing cyber threats are as real for an average computer user or bank customer as it is for big businesses and financial institutions.
Banking and telecom nexus
In the first part of this investigation, mid-day had exposed how cyber criminals are harvesting customer data to carry out financial frauds. The fragile digital security cover in leading banks, BPOs, and telecom service providers are resulting in incidents of data breach becoming commonplace in Mumbai. Most of the high-profile institutions are ignoring blatant weaknesses in the protocol levels in their applications, websites and payment gateways, leaving customers to conduct transactions in a high-risk environment.

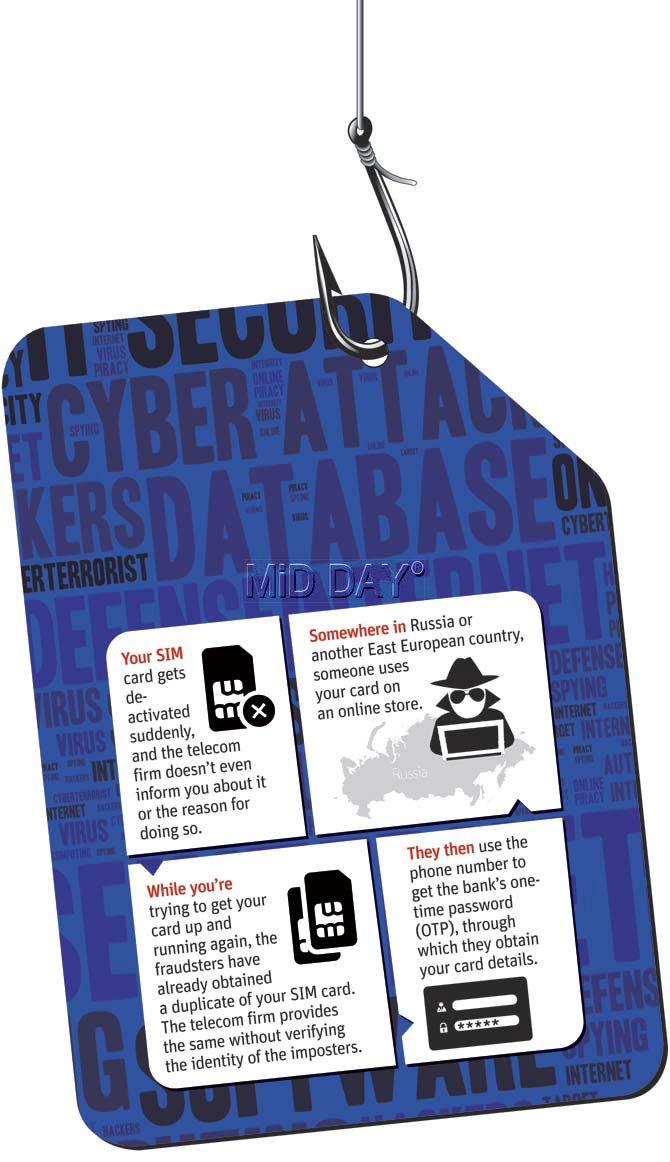
Vijay Kulkarni's phone was de-activated suddenly
The continuing investigation shows that a nexus of banks and telecom companies, who claim their card and vendor system to be PCIDSS (Payment Card Industry Data Security Standard) certified, are making no effort to secure their electronic payment gateways and systems in place to respond to card frauds.
Their apathy is leading to a spate of recent financial frauds with a simple modus operandi: where the fraudsters somehow get the victim’s SIM deactivated and then obtain a duplicate card. The duplicate SIM is then used to obtain a one-time-password (OTP) and the innocent customer’s account is used to make fraudulent payments in a foreign country, mostly Russia. Nobody knows why Russia has been a preferred choice of these transactions.
Vijay (68) and Sushama Kulkarni (65), a couple from Mumbai, found that six transactions worth a total of Rs 1.4 lakh had been made from their SBI credit card within half an hour, on a little-known online store in Russia (sprypay.ru.petrozavodsk) in the wee hours of July 1, 2013. Throughout 2014, six more cases in the city were reported where credit cards of customers were cloned and misused by fraudsters in Russia.
“Clearly, in this case, the banks did not give any meaningful, detailed report about the internal investigation into the crime by their Fraud Investigation Unit (FIU). They have not been able to explain through use of logs how the customer credentials got leaked out in the case,” said the Kulkarnis.
In all these cases, the customer’s mobile services were abruptly discontinued by the telecom service provider at the behest of the imposters whose identities were never checked by the firms, and a duplicate SIM was issued to fraudsters who conveniently used it to obtain a one-time-password (OTP) from the customer’s phone number registered with the bank.
mid-day investigation: Hooch being made inside SGNP
Clearly, in the case of the Kulkarnis, the bank and telecom companies failed to explain how customer data was leaked. Seconding the Kulkarnis’ contention, the state adjudicating officer, in a report dated February 28, 2014, noted that, “Banks do not seem to have any monitoring system to alert their FIUs about suspicious transactions.”
“While the state AO ordered the bank to pay the Kulkarnis, instead of honouring the verdict of lower court, the respondent (SBI) chose to appeal to the cyber tribunal in Delhi. Ethically, they should first pay the victim and then proceed for a higher appeal,” said Prashant Mali, the couple’s lawyer in the case.
Banks, telecom firms not protecting their customers
An analysis of the 102 cases registered under Section 46 of the Information Technology Act, 2000, during 2013 and 2014, shows that in 5-6 cases, credit cards of customers were cloned and misused in Russia or an East European country, but not before their critical data was leaked from banks and telecom firms.
The services of the SIM card in most of these cases were suddenly discontinued without informing the customer, and without verifying credentials, were reissued possibly to fraudsters. Several government reports have pointed out to this fact; that customer data was leaked, phone SIM details altered just before the incident. “In many a case brought before me, financial frauds have been committed by fraudsters using the registered mobile numbers of the banks’ account holders.
By not implementing security procedures, the telecom companies are jeopardising the sensitive and personal data of all its customers and in a way abetting in commission of frauds related to financial transactions,” Rajesh Aggarwal told mid-day, adding, “There is an undeniable direct nexus between blocking of SIM card of the complainant, issuance and use of the duplicate SIM card by the fraudster, and unauthorised financial transactions from the account of the complainant.
In fact, the bank transactions happened after the duplicate SIM card was procured and activated by the fraudster.” Aggarwal is no more with the state and has moved on to Central duties. The banks are doing little to make the electronic channels safer. In the West, a lot of protection is offered to customers by Internet websites during transactions; in the United States, banks insure customers against online and ATM frauds beyond a liability of $50 under Section 909 of the Electronic Fund Transfer Act, making it loaded in favour of the customer.
The Reserve Bank of India, on similar lines, issued the “Code of Bank’s Commitment” in January 2014, making customers of such fraud liable to the extent of Rs 10,000 while the bank has to make good on the rest of the amount. So, if the loss is Rs 1 lakh, the customer will bear a liability of only Rs 10,000 and the bank, Rs 90,000. But no bank is following this code, industry sources said.
“A reflection of their negligence is that they (banks) have started availing our company’s services to prepare an Incidence Report soon after every financial fraud. This, too, with a focus only on identifying mistakes made by the customer and reducing the liability of the bank in case of a fraud,” said Sahir Hidayatullah, a digital risk entrepreneur and ethical hacker from Mumbai.
Upon receiving a complaint of fraud from the customer or the card holder, most of the banks do not carry out any internal investigation through their Fraud Investigation Unit. Rarely do they take action. These banks do not have consumer-friendly policies or mechanisms to safeguard the consumer’s interest. In a scathing report of case number 39, the adjudicating officer’s report recorded these facts from a credit card fraud case:
“Both SBI and Bharti Airtel, two big names in the banking and telecom sector respectively, have badly let their customers down, and are totally non-repentant about their laxity, bordering on connivance, which has resulted in this crime,” an internal report of the state noted.
Pay up or lose your data
Hyderabad-based legal counsel, Kokkula Srinivas, nearly compromised his entire data along with his personal information and critical financial records after he found his system locked and encrypted with an RSA algorithm in December 2014. RSA is a public-key crypto system used for secured data transmission, and was created in 1977 by computer engineers Ron Rivest, Adi Shamir and Leonard Adleman; the name RSA is drawn from the initials of their surnames.
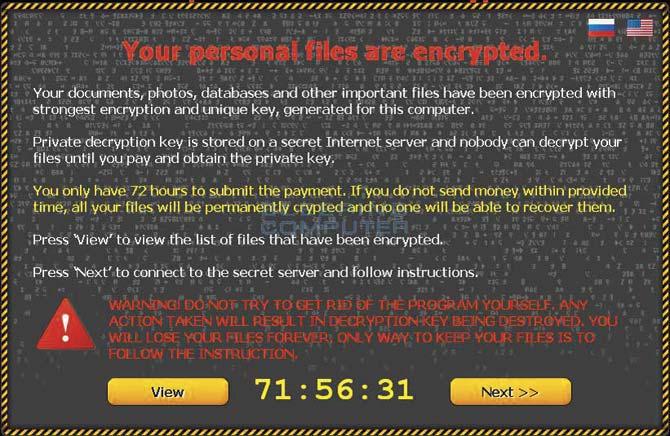 A screen grab of the CTB-locker, the latest ransomware that is affecting users in Mumbai
A screen grab of the CTB-locker, the latest ransomware that is affecting users in Mumbai
Srinivas’ data was locked by a latest version RSA-2048, which demanded a handsome sum in European currency in return for the decryption key for the coded encryption. “The structure and data within your files have been irrevocably changed, you will not be able to work with them, read them or see them, it is the same thing as losing them forever, but with our help, you can restore them,” read the warning on Srinivas’ system.
The only option he was left with was to either pay up or risk losing his entire hard disk. “I felt helpless. This was a spam attack that possibly took place soon after my son had watched and downloaded something from YouTube. My entire system and hard drive was locked and they were demanding a ransom in exchange,” he told mid-day, adding that he refused to pay up and lost his entire data in this attack.
Indian computer users are being warned of this mass spamming attack that aims to encrypt their computers and extort sums to unlock it. These emails come masquerading as communications from banks, and are used to mostly target small businesses and individual users. The emails have an attachment with a malicious program that, on opening, encrypts the user’s hard drive. It then displays a countdown time, while demanding ransom for a key.
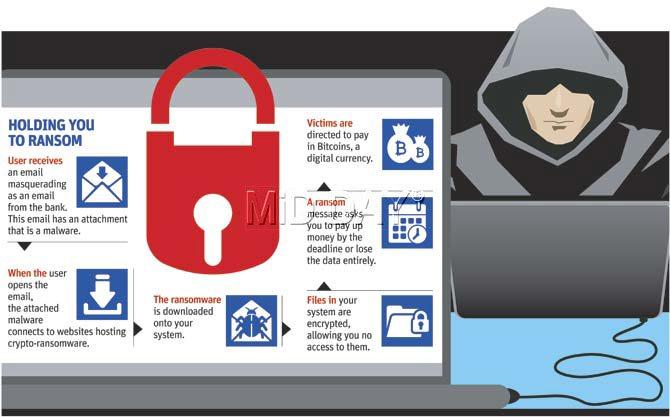
While such “ransomware” is not new, the Cryptolocker malware being used against unsuspecting users is becoming commonplace. The most common Cryptolocker targeting users in Mumbai, according to the cyber police, is CTB-Locker, a latest data-encrypting ransomware. Upon encrypting the files, the virus will create a .TXT and .HTML file with instructions on how to obtain the decryption key (a key to unlock the device), which will be available after paying the ransom starting from a basic 3 Bitcoins and going into hundreds.
Bitcoin is a form of digital currency that can be purchased online. The decryption key will only be valid for up to 96 hours; after that time, the server will delete the key, and the files will remain encrypted. One Bitcoin, sources said, could be worth anywhere over Rs 40,000. “The tragedy is that the Indian IT Act is silent on Bitcoins, while the RBI does mention it in passing in some circulars as ‘dangerous’.

Recently, a diamond merchant in the city found that his cellphone was loaded with spying software. A rival had installed it to cause financial losses. Cyber experts say select mobile phone technicians in the city have turned illegal software installers. Pic for representation/Thinkstock
In countries like Canada, it has been recognised as a currency and there are even ATMs for those who want to access it legally. When our laws do not even recognise it, how do we curtail it or its use or misuse?” questioned Pune-based cyber law expert and dean of Asian School of Cyber Law (ASCL), Rohas Nagpal.
A May 2015 report of security research firm Symantec has placed India third in the list of ransomware attacks in Asia, with an average of 170 attacks a day or total 60,000 in a year. An estimated 86 per cent of these ransomware attacks were Crypto-ransomware. Smaller businesses of the size of 1-250 employees received a virus-bearing email every 370 emails, twice the number compared to their larger counterparts.
“While we are regularly getting complaints and investigating some cases of ransomware attacks on individual users, only a few people have officially registered an FIR against a CTB attack,” said P Warke, a police officer and ransomware expert in Cyber Cell, Mumbai Police.
Recently, a city-based diamond merchant’s mobile phone was loaded with spyware, and his conversations were recorded, including bank and other financial details. He reported the incident to private investigators in January 2015. “We found that the bug was installed by a rival trader who wanted to cause financial losses to the victim.
We scanned the phone through various detection tools and found it bugged,” said Sachin Dedhia, a private fraud investigator and founder of Skynet Secure, a company that investigates mobile phone hacking.
Mobile malware, voice recording apps and spyware continue to sell openly in Mumbai, while the law-enforcing agencies do nothing about it. “In selected corners of the city, several mobile phone repair technicians have become illegal software installers. They are earning more money by installing illegal software and spyware than selling smartphones.
Nearly 95 per cent of the people going to these shops to get their mobile phones fixed, end up buying voice recording software and discreet video recording software, which does not show the video screen and allows them to do discreet recording in public,” said leading cyber law expert and advocate, Prashant Mali.
Mobile malware are capable of collecting information related to application programming interface (API) keys, GPS location, international mobile equipment identity (IMEI) numbers, network operator and other key details of a device. The main way for these infections are SMS-related malware attacks, especially in Android phones, or as an APK file, a type of file for the Android operating system.
The spyware, used to record voice, intercept conversations and video recording from a device, are easily available in Mumbai’s shops. The mobile malwares and spy software selling openly in Mumbai are: Andorats, Mspy, Flexispy, which are available online at $149, $200, and $349 respectively. Some shops in Mira Road are openly selling for Rs 1,000 to Rs 5,000 steganography software, which is software used to hide files behind images.
A February 2015 report by Finnish security firm F-Secure ‘The start of Internet in India-2014’ said about 22 per cent of total mobile phones in Mumbai were likely to be infected by malware, followed by Chandigarh and New Delhi. “Most of these are purchased to hide corrupted files behind social messages.
The common method is to hide corrupted files behind messages and images related to religion, good luck charms, and those related to board exam messages. These files are less than 1-MB size, and there are as many as 57 kinds of virus that could be attached in Android phones; some of these can even be hidden behind popular Android-based games like Temple Run,” said a mobile seller from Mira Road who deals in mobile spyware.
 Subscribe today by clicking the link and stay updated with the latest news!" Click here!
Subscribe today by clicking the link and stay updated with the latest news!" Click here!






