The latest barrage of cyber attacks to strike India this month is seeing hacker communities from countries who have a bone to pick with ours get back by leaking your personal data

Illustration/Uday Mohite
On March 2, Mysterious Team Bangladesh (MTB), a hacker group known to target India in the past, launched a new wave of cyber-attacks on a wide range of Indian websites, and dumped their data on their dark web forum as well as on their Telegram channel. The group also sent out a clarion call to all its affiliates asking them to join ‘Op India’, and by March 16, two more hacker groups, Team Insane PK (affiliated to Pakistan) and The Yemeni Ghost, had joined forces with MTB.
ADVERTISEMENT
This is the third wave of cyber-attacks that India has witnessed in less than a year. In June 2022, DragonForce Malaysia launched an attack on Indian websites as retribution for former BJP spokesperson Nupur Sharma’s objectionable remarks against Prophet Mohammed. In November 2022, MTB launched its first wave of cyber-attacks. In January 2023, some Indian hacker groups formed an alliance to get back at Bangladesh, defacing the country’s websites and breaching its data. The current cyber-attack is counter-retaliation to these attacks.
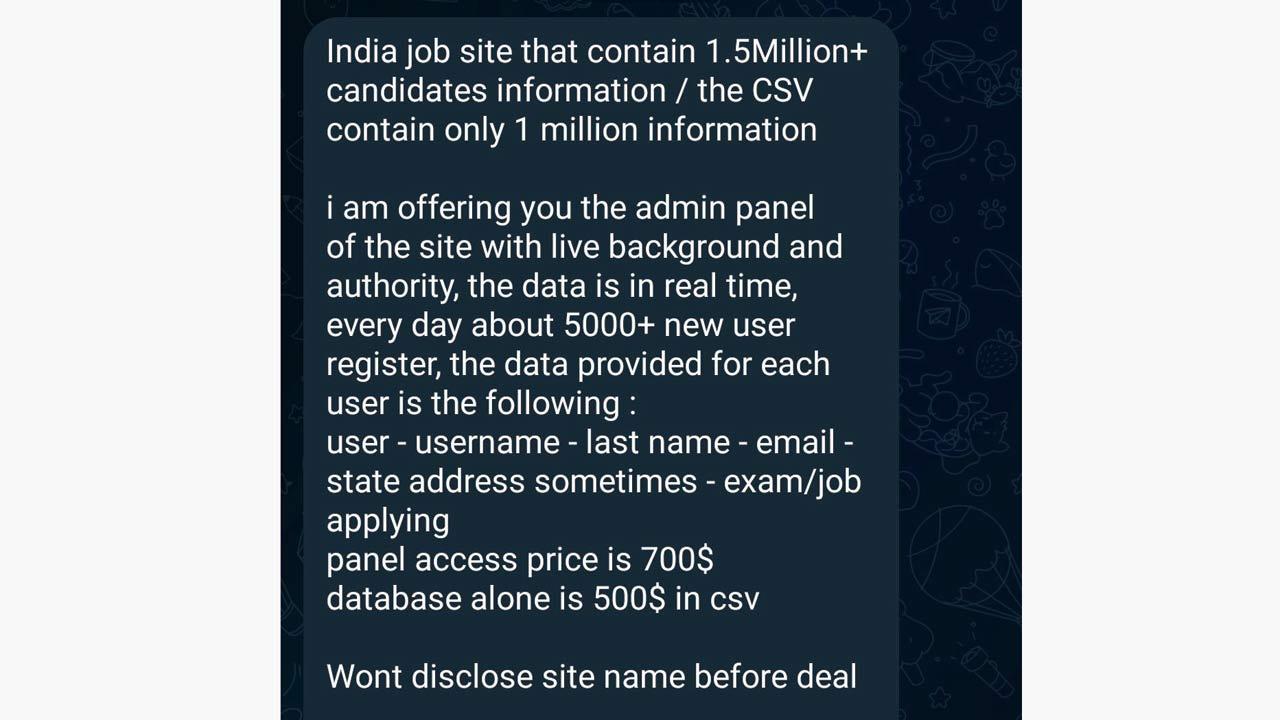 A post on a dark web forum offering data of more than 1.5 million candidates hacked from an Indian job site for sale
A post on a dark web forum offering data of more than 1.5 million candidates hacked from an Indian job site for sale
The result: Several gigabytes of data, that directly affect the common Indian citizen, are now up for grabs on the Internet. And this is but a drop in the already massive ocean of data freely available online for all to use, and misuse.
Known as breached data, this information, which used to be the most sought after commodity on the dark web, can now be downloaded at the click of a mouse. This includes names, login IDs, passwords, e-mail IDs, residential addresses, social media account information, PAN card information, Aadhaar and mobile numbers—commonly called Personally Identifiable Information (PII), all of which combined can effectively lay a person’s entire life bare.
 Ritesh Bhatia
Ritesh Bhatia
To add to the concerns of cyber security experts and law enforcement officers, data that is not available for free is available at nominal prices on dark web chat forums and Telegram channels. Hacker groups routinely upload advertisements to platforms such as Breached Forums, offering small samples to prove authenticity.
And if the required data is not available for free or through advertisements, all you have to do is ask...
On March 11, a user on a hackers’ Telegram channel posted, “Who needs Disney Plus?” and offered log-in credentials for the popular online streaming platform. Another user replied saying, “Me”, to which the response was, “Text me”. As is the protocol for price negotiation and sale, the conversation then moved to personal chat.
This was just one of scores of such exchanges seen on these forums on a daily basis, where sale of data is decided in under a minute.
The perpetrators of the ongoing cyber-attack have so far hacked websites of 70 Indian entities, including banks, educational institutes and government departments. The first phase included just disabling the websites (which were restored within a day), after which the hackers moved on to extracting data and dumping it online. Over the last fortnight, the hackers have dumped PII of college students, job applicants to the Railways, an NGO, and a medical association, and confidential letters recommending action against government servants, hacked from a central government website.
“The biggest risk,” says cyber expert Ritesh Bhatia, “and the highest priority for threat actors, in data breaches, is identity theft. Using names, mobile numbers, Aadhaar or PAN numbers and photographs from different sets of data, cybercriminals can create completely new identities which can be used for a wide variety
of crimes.”
On March 4, the Delhi Police arrested five persons who allegedly obtained virtual credit cards in the names of Abhishek Bachchan, Shilpa Shetty, Madhuri Dixit and Mahendra Singh Dhoni. They had applied for a virtual credit card with Pune based company, One Card.
The police found that the accused simply went online and looked up the celebrities’ PAN Card numbers. They combined these with their own Aadhaars, addresses, photographs and submitted their applications. When One Card’s algorithm verified the applications against the PAN Card numbers, it led to the celebrities’ high CIBIL scores. On this basis, the accused managed to get credit limits of up to R6 lakh each, and immediately made purchases worth over Rs 21 lakh.
“This is just one example where the fraud was flagged and the accused were arrested,” says Bhatia. “There have been cases of people obtaining addresses of women through breached data sets, sending flowers to their homes with the intention of creating rifts in their marriages, and then extort money in exchange for leaving them alone. There are umpteen more serious scenarios, like criminals, using PII of customers from breached data of companies, making ID cards and walking into the company premises.” As he spoke to mid-day, Bhatia entered a random name on a data breach website and came up with 12 entries of the person’s passwords being leaked over the years, from 12 different accounts.
Cyber police officers say that apart from identity theft, the exposure of phone numbers and email IDs exposes victims to a wide range of phishing scams to which many fall prey every day. Even as you read this, hundreds of us are receiving text messages, purportedly from our banks, asking us to update PAN numbers in KYC details. With the message comes a link that steals the victim’s netbanking credentials, siphoning lakhs of rupees from her/his accounts. The free availability of mobile numbers provides a ready database of potential victims to cybercriminals, officers say.
A quick sweep of Breached Forums, one of the world’s largest databases of stolen and breached data, reveals 1,400 crore records from 888 data sets breached from all over the world since as far back as 2007. These are still available to download and use for free, including 3.1 crore records of Rail Yatri users from a 2022 breach; 28.6 crore records of Truecaller India users from a 2019 breach; and 41 lakh records from a 2021 IIM Jobs applicants’ data breach. Further, there are non-country specific databases from utilities and services used the world over.
Data for February 2023 compiled by Surfshark, a cybersecurity company based in the Netherlands, shows that over 100 crore data points hacked or leaked from Indian servers since 2004 are available on the internet even today. A data point is any form of data directly connected to a user. Surfshark also found that, based on information collected by their data breach monitoring tools, India ranks second in Asia and eighth in the world in terms of breached data since 2004, with data of 28.88 crore users being affected. It also found that just in 2022, a total of 47 lakh Indian Internet users were affected, and that around four data points are leaked from a single account on average, with passwords being among the most leaked data points.
“Our monitoring tool,” says Surfshark’s lead researcher Agneska Sablovskaja, “contains publicly available information about personal data that’s been copied, transmitted, viewed and stolen, or illegally used since 2004. The data sets are found in various places online, such as hacker forums.” According to their data, since 2004, over 15.17 crore passwords, 8.45 crore password hashes, 8.31 crore first names, 8.33 crore phone numbers and 8.17 crore names have been leaked. A password hash is a password stored in encrypted form by the website. While the advantage is that the actual password is never recorded on the server, the flip side is that even hashes have to be stored somewhere. In the wrong hands, decrypting them is just a matter of using the right software.
Researchers at CloudSEK, a Bengaluru based cybersecurity research firm, have been tracking MTB’s activities since their first attack in 2022. “From our evaluation,” says Abhinav Pandey, Cyber Threat Researcher at CloudSEK, “MTB seems to be an evolving hacker group, with young members using existing vulnerabilities. Most of the websites they hacked were restored within 15 to 20 minutes, and only the smaller banks were offline for an entire night. However, with the kind of support they are getting from other hacker groups, they might become a bigger concern in the days to come, especially if they get endorsement from a state-sponsored hacker group hostile to India.”
But as days pass, the data of more citizens is breached and exploited.
The fact is not lost on the hackers. The pinned message on the MTB Telegram channel reads, “We are apologies to Indian innocent people for some inconvenience. We has been not targeting India and not attacking your country Cyberspace after 2022. But your country some noobs attacking our country Cyberspace without any reason, for this we are launching a cyber attack in your cyberspace. We are telling you before that don’t mess with us kids (sic).”
1,07,29,54,023
Data points of Indian users exposed in breaches since 2004
Statistics of leaked data points
Passwords: 15,17,20,911
Password hashes: 8,44,61,802
First names: 8,30,98,309
Phone numbers: 8,33,07,228
Full names: 8,17,28,445
Courtesy: Surfshark
 Subscribe today by clicking the link and stay updated with the latest news!" Click here!
Subscribe today by clicking the link and stay updated with the latest news!" Click here!







